Duplicating locked EEPROM data from a microcontroller (MCU) like the PIC18F8410 can be a challenging task, especially when the data is secured or encrypted. The EEPROM stores critical information such as firmware, configuration data, and calibration parameters, which are vital for the microcontroller’s operation. In cases where the data is locked or protected, hackers and reverse engineers often use techniques to attack or crack the protection mechanism.
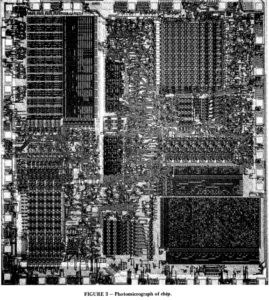
One of the first steps in recovering locked EEPROM data is to attempt to decapsulate the MCU, removing the protective layers around the chip to gain physical access. Once exposed, experts can use specialized tools to dump the memory and extract the binary data. If the firmware is encrypted or locked, it may require decrypting or decoding to make it usable. Reverse engineering techniques are often employed to analyze the source code or firmware stored in the EEPROM, helping hackers replicate or clone the microcontroller’s functionality.
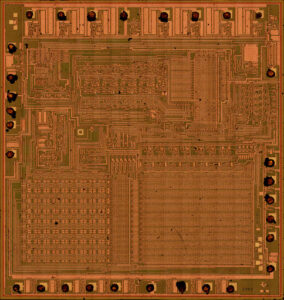
Alternatively, using a hacker’s technique to probe the flash memory or program directly can sometimes bypass locked protections. If successful, the extracted data can be replicated, allowing the MCU to be cloned or restored. However, it’s important to note that cracking or attacking secured systems is illegal and unethical in most cases, and such activities should only be performed with permission for recovery purposes.
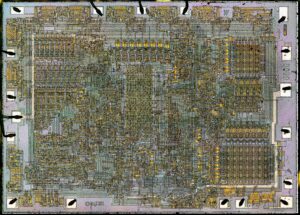
We can Duplicate Locked MCU PIC18F8410 Eeprom Data, please view the MCU PIC18F8410 features for your reference:
Do not use theMOVFF instruction to modify any of the interrupt control registers while any interrupt is enabled. Doing so may cause erratic microcontroller behavior.
Interrupt flag bits are set when an interrupt condition occurs, regardless of the state of its corresponding enable bit or the global interrupt enable bit of Copying Microchip PIC16F59 Program. User software should ensure the appropriate interrupt flag bits are clear prior to enabling an interrupt when Duplicate Locked MCU PIC18F8410 Eeprom Data.
This feature allows for software polling. Interrupt flag bits are set when an interrupt condition occurs, regardless of the state of its corresponding enable bit or the global interrupt enable bit by Copy Microcontroller PIC12F510 Program. User software should ensure the appropriate interrupt flag bits are clear prior to enabling an interrupt.
This feature allows for software polling. The PIR registers contain the individual flag bits for the peripheral interrupts. Due to the number of peripheral interrupt sources, there are three Peripheral Interrupt Request (Flag) registers (PIR1, PIR2 and PIR3) if Duplicate Locked MCU PIC18F8410 Eeprom Data.
Note 1: Interrupt flag bits are set when an interrupt condition occurs, regardless of the state of its corresponding enable bit or the Global Interrupt Enable bit in the process of Extract Secured PIC16C71 Heximal, GIE (INTCON<7>).
2: User software should ensure the appropriate interrupt flag bits are cleared prior to enabling an interrupt and after servicing that interrupt of MCU Cracking.

