In today’s competitive electronics market, many companies face challenges when the firmware of their microcontrollers becomes inaccessible. One common issue is dealing with the copy locked MCU PIC18F8393 firmware. This secured and protected firmware is designed to keep its flash memory, EEPROM, and associated data safely encrypted. However, when the original source code is lost or damaged, our advanced recovery service can help you regain access without compromising the chip’s integrity.
Our service employs a comprehensive suite of techniques including crack, attack, decapsulate, hack, decrypt, decode, reverse engineering, recover, replicate, clone, extract, and dump. These methods are applied only on a legally authorized basis and are intended to assist clients who have rightful ownership of the microcontroller. By leveraging sophisticated procedures, our team can analyze the secured binary and memory file of the PIC18F8393 chip to retrieve the embedded program data.
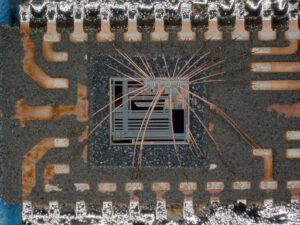
The process begins with an in-depth evaluation of the microcontroller’s architecture. Special attention is given to its protected flash memory and EEPROM, where the critical binary data or complete firmware archive is stored. When necessary, we decapsulate the chip in a controlled environment to physically access the secure components. Once access is achieved, we carefully extract or dump the program data without altering the original memory content.
After the extraction phase, our experts decrypt and decode the encrypted firmware. Through meticulous reverse engineering, we recover the functional structure of the program. This stage not only replicates the firmware for backup purposes but can also clone the necessary features, allowing for further analysis or even restoration of lost source code. The entire operation is performed under strict quality control, ensuring that the process adheres to legal and ethical standards.
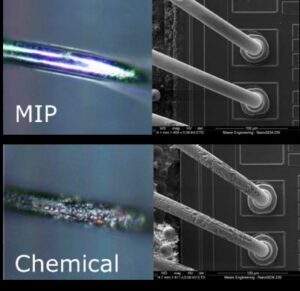
It is important to note that while our approach incorporates techniques such as hacking and reverse engineering, we perform these tasks solely for clients who have proper authorization. This service is designed to protect your intellectual property and restore critical data from a secured microcontroller.
By choosing our advanced recovery service for copy locked MCU PIC18F8393 firmware, you are ensuring that your embedded system’s integrity remains intact while gaining access to essential firmware data for operational continuity.
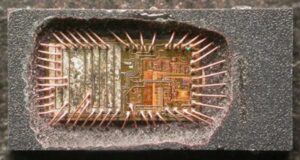
By choosing our advanced recovery service for copy locked MCU PIC18F8393 firmware, you are ensuring that your embedded system’s integrity remains intact while gaining access to essential firmware data for operational continuity.
We can Copy Locked MCU PIC18F8393 Firmware, please view the MCU PIC18F8393 features for your reference:
We can Copy Locked MCU PIC18F8393 Firmware, please view the MCU PIC18F8393 features for your reference:
When the IPEN bit is cleared (default state), the interrupt priority feature is disabled and interrupts are compatible with PICmicro® mid-range devices. In Compatibility mode, the interrupt priority bits for each source have no effect. INTCON<6> is the PEIE bit, which enables/disables all peripheral interrupt sources to facilitate the process of Read Out Microcontroller PIC16F690 Program.
INTCON<7> is the GIE bit, which enables/disables all interrupt sources. All interrupts branch to address 0008h in Compatibility mode. When an interrupt is responded to, the global interrupt enable bit is cleared to disable further interrupts to Crack MCU. If the IPEN bit is cleared, this is the GIE bit. If interrupt priority levels are used, this will be either the GIEH or GIEL bit when Copy Locked MCU PIC18F8398 Firmware.
High priority interrupt sources can interrupt a low priority interrupt. Low priority interrupts are not processed while high priority interrupts are in progress. The return address is pushed onto the stack and the PC is loaded with the interrupt vector address (0008h or 0018h). Once in the Interrupt Service Routine, the source(s) of the interrupt can be determined by polling the interrupt flag bits when Copy Microcontroller PIC12F510 Program.
The interrupt flag bits must be cleared in software before re-enabling interrupts to avoid recursive interrupts. The “return from interrupt” instruction, RETFIE, exits the interrupt routine and sets the GIE bit (GIEH or GIEL if priority levels are used), which re-enables interrupts after Copy Locked MCU PIC18F8398 Firmware.
For external interrupt events, such as the INT pins or the PORTB input change interrupt, the interrupt latency will be three to four instruction cycles by Extract Secured PIC16C71 Heximal. The exact latency is the same for one or two-cycle instructions. Individual interrupt flag bits are set, regardless of the status of their corresponding enable bit or the GIE bit.

