Extract Heximal of Protected Microcontroller PIC18F6622
Extract Heximal of Protected Microcontroller PIC18F6622 from its memory like flash and eeprom, program and data will be decoded and replicated, the MCU PIC18F6622 can
Extract Heximal of Protected Microcontroller PIC18F6622 from its memory like flash and eeprom, program and data will be decoded and replicated, the MCU PIC18F6622 can
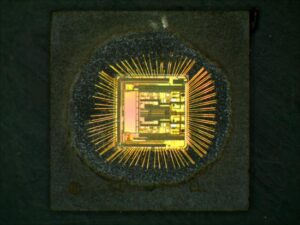
Extract Code from Locked MCU PIC18F6527 memory like flash and eeprom, program and data will be integrated and readout the file in the format of

Extract Code from Encrypted MCU PIC18F6410 embedded memory needs to disable its security fuse bits and get access to its databus which is connected the

Encrypted Microprocessor PIC18F4682 Code Extraction starts from cracking MCU memory include flash and eeprom, after this process the status of Microcontroller will reset from encrypted
Extract Heximal of Secured MCU PIC18F4610 from its flash and eeprom memory, the status of Microcontroller has been modified from locked to unlocked one; Indirect

Extract Code of Encrypted Microcomputer PIC18F4553 in the format of binary or heximal, in order to locate the security fuse bits on the MCU which

Extract Embedded Code from Protected Chip PIC18F4525 which include the eeprom data and flash program, the microcontroller PIC18F4525 reverse engineering process will take 1-2 days

Extract Code From Protected MCU PIC18F4515 and clone to other blank MCU which will provide the exactly same functions as original version; There may be
